Security Conscious Wireless Sensor Network Architectures
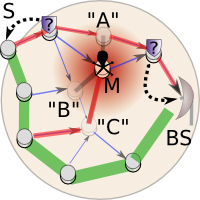
This project will investigate the field of security in wireless sensor networks. Wireless sensor networks have the ability to gather data economically in other inaccessible locations, but the data that is returned must be trustworthy for networks to be viable. The security issues on the Internet have made it clear that it is impossible to retrofit security into already designed and implemented systems. In almost every significant sensor network deployment envisaged it is possible to imagine adversaries who may attempt to subvert the network. This could be done in many creative and insidious ways: adding malicious nodes, jamming signals, tunnelling transmissions are all ways in which the an attacker could easily disrupt the strategic objectives of an unprotected sensor deployment.
Normally cryptography can be relied upon to protect confidentiality, integrity and availability of data in communication systems. However, the situation is complicated by the power constraints and low memory capability of WSN systems, as well as the inability to always contact centralised trusted parties in dynamic networks. Together with the ability of attackers to remove unattended nodes from the network and compromise their key information, reprogram them or add new hardware, the usual remedies of centralised keying schemes (which put the burdens of management on a single coordinator) are less appropriate. Nodes must instead judge each other's actions to attempt to determine intent and behaviour.
Cross-layer metrics from which potential attacks could be detected include packet loss rates, static and dynamic disturbance metrics (node or traffic density in regions), interference levels, frequency of violations, of intended protocol, node density changes, and patterns of changes to route metrics. The challenge will be to produce an architecture which can accomplish all of this within a poorly resourced sensor network environment.
Areas of investigation
- Uncovering cross-layer signature traces which reveal particular attacks with high reliability, and distributed metrics for trust rating, and how to modify protocols to incorporate and make decisions based upon them. So far, this has concentrated on using the disturbance metrics for wormhole attack avoidance, but will now be expanded to investigate other combinations of attack and signature.
- Using the metaphor of a distributed database to share security state
- in advance, to make more resilient routing decisions ahead of potential attacks.
- Quantifying the energy, latency and other costs of such security measures, and working to minimise their impact on overall network performance.
- As a more speculative extension, exploring the concept of active agents to proactively investigate the network and form and refine hypotheses of attacker locations and intent. This will incorporate ideas from the intelligent systems community.
It is expected that the project will rely heavily upon simulation, and a custom network simulator will be developed to flexibly model security interactions. Analytic techniques will be used where appropriate to add rigour and strengthen the performance and stability guarantees provided by any custom algorithms developed.
Members
- James Harbin
- Paul Mitchell
- Dave Pearce
Dates
- October 2007 to
September 2011
Research
